A mobile bitcoin wallet is convenient to use, because it can be
installed on either a tablet or smartphone. Either of these devices is
more often than not in close proximity to everyday consumers and doesn’t
require users to take additional items with them wherever they go.
Similar to how a desktop bitcoin wallet works, having access to an
Internet connection — either through mobile data or WiFi — is a great
plus when it comes to sending and receiving transactions. However, this
is not a must, as most bitcoin wallets allow users to send and receive
funds through NFC or Bluetooth Low Energy connection. In return, this
makes mobile wallets more versatile compared to their computer
counterparts, which is also part of the reason why bitcoin has received a
lot of appreciation from its users.
In terms of security, the story with mobile bitcoin wallets is not
all that different from a piece of software installed on your computer.
The private key — which allows you to spend bitcoins from your wallet —
is stored on your mobile device itself. As a security measure, this
reduces the risk of the private key falling into the wrong hands.
However, there is a potential risk in doing so as well. Given the
current rate at which technology — and consumer behavior — evolves,
smartphones and tablets are being replaced at a rapid pace. Considering
that your private key is stored on that mobile device, it is important
to make a backup as soon as you install the mobile bitcoin wallet of
your choice.
Depending on which type of mobile wallet you’re using, a backup
feature is included in the software itself. A copy of your backup can
then be exported to cloud services such as Dropbox or Google Drive, or
even sent to yourself via e-mail. Any application you have installed on
your mobile device with backup capabilities should be available to use.
All in all, mobile bitcoin wallets can provide the best solutions
when balancing the needs of security and convenience, but it all depends
on the individual user in the end. If users are careless with their
device, or forget to back up their private key, there is no option to
restore access to their mobile bitcoin wallet. Bitcoin allows users to
take full control — and full responsibility — at every step, which
includes responsibilities such as backing up their mobile wallet.
Secure online bitcoin wallets — or not
You could easily draw a parallel between online bitcoin wallet
providers and financial institutions such as banks. Both services handle
your personal funds, and you can check the balance, as well as send and
receive funds at any time. But you are trusting a bank to keep your
funds safe, and that’s not what bitcoin is about. Ever since bitcoin’s
inception, trust has played an integral role in the development of this
ideology.
Satoshi Nakamoto envisioned that the future development of bitcoin
would eventually lead to a “trustless” society, where all interactions
were done between people directly, without using any third-party
service.
On top of that, you are responsible for protecting your personal mobile
wallet service account. Most online bitcoin wallet platforms provide
options such as two-factor authentication. And although that additional
layer of security protects the user from harm — in most cases,
as no system is truly perfect — it will not prevent your funds from
being stolen if the online wallet service itself is hacked.
Secure paper bitcoin wallets
A bitcoin paper wallet can be best described as a document containing
all the data necessary to generate private keys, effectively forming a
“wallet of private keys.” But that is not its only purpose, because a
paper wallet can also be used to store bitcoins safely and securely, in
which case the paper itself also includes public keys and redeemable
codes.
The main purpose of a redeemable code is to use it as a means of
funding and “redeeming” funds associated with a certain bitcoin wallet
address. However, it is important to note that paper wallets should only
be used once, because a paper wallet is not a bitcoin wallet intended
for daily use.
Paper wallets can serve many purposes. A bitcoin paper wallet makes
for a great gift when introducing friends, family, and loved ones to
bitcoin. Or you can give someone a paper wallet as a tip, to show your
appreciation for something the other person has done. Redeeming a paper
wallet as a gift or tip requires recipients to have a bitcoin wallet
installed on their computer or mobile device, through which they can
import the private key associated with that address.
 Once your project is created successfully, you will have the following content in your Project Explorer −
Once your project is created successfully, you will have the following content in your Project Explorer −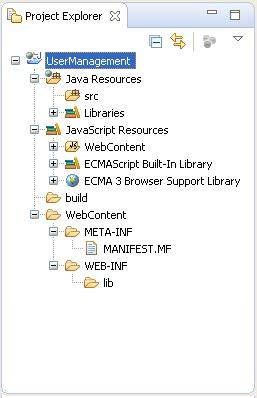
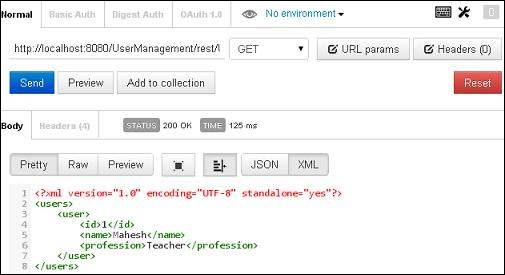 Congratulations, you have created your first RESTful Application successfully.
Congratulations, you have created your first RESTful Application successfully.